What is DKIM?
DKIM serves as an essential email authentication protocol that operates similarly to a digital signature. By embedding encrypted code in the email header, DKIM enables mailbox providers (MBPs) like Yahoo and Gmail to verify the authenticity of the sender’s domain and ensure the email truly originates from an authorized user.
Unfortunately, email spoofing has become a growing concern in recent years, leading to various scams. These fraudulent emails often impersonate reputable companies such as PayPal, Amazon, FedEx, or banks, with the intention of tricking recipients into clicking malicious links or divulging sensitive information.
DKIM plays a crucial role in safeguarding recipients from such scams by allowing MBPs to distinguish between legitimate senders and impostors. Additionally, it guarantees that the email content remains unaltered during transmission.
While achieving a 100% email deliverability rate may seem ideal, it is important to block illegitimate emails to protect users from potential harm. Therefore, ensuring the proper implementation of DKIM significantly enhances the likelihood of legitimate emails reaching their recipients and helps combat email-related threats effectively.
DKIM Format
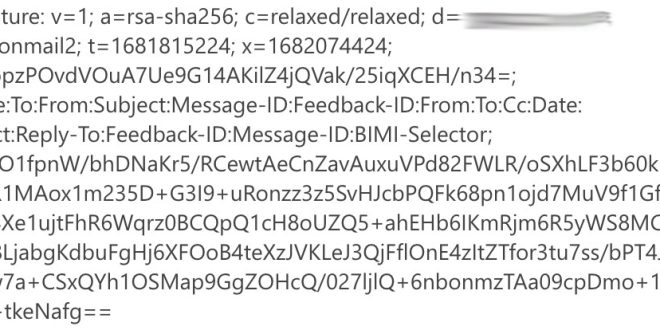
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=ittreasure.net; s=default; t=1572282571; bh=NFzBvJ/pEmf+yUHDd/Y7dYNH9pE+Bx6o95KcxhwFL78=; h=From:To:Subject:From; b=QwgINKqwcBu3GbeWm2Be81qXks6Pq9yMmDZl9C6mT8moXVBeokpEmDN+0RyZFiOmNH30kbe6HbS2lY3b1Pf726UH/V/0VAH0nigTuir4TWdN/IUePV+goQdEJ2+sDQ1fHlVjyyJCRwCiFiZpBIjhTBNN0vrgNJZ/gSLLOvq6k3s=It consists of the following tags:
- v=1 – the version (always equals to 1)
- a= – a signing algorithm used for the creation of a DKIM record
- c= – a canonicalization algorithm for the header and the body
- d= – a domain where the DKIM is signed
- s= – a DKIM selector
- t= – a timestamp of when the email was signed
- bh= – a hashed email body
- h= – a list of headers
- b= – a digital signature
To create the DKIM signature, you will have to specify only two tags of all the above: an authorized domain (d=) and a selector (s=).
Authorized Domain (d=)
During the DKIM signature validation process, the recipient’s mail server verifies if the domain specified in the DKIM signature (d=) corresponds with the domain mentioned in the ‘From:’ field of the email. Since it’s common to use different domains for various types of emails, it becomes crucial to ensure that each domain is authorized.
Please note that when utilizing different domains for sending emails, it is necessary to set up distinct DKIM signatures for each domain to maintain proper authentication and email deliverability. By doing so, you can establish the authenticity of the sender and safeguard the reputation of each domain used in your email communication.
Selector (s=)
To create a DKIM key, you must specify a selector or a selector prefix, which serves as a unique identifier. During the validation process, the recipient’s server initiates a DNS query based on the combination of the authorized domain (d=) and the selector (s=) to retrieve the corresponding public key.
Each selector is associated with a distinct private key. When sending various types of emails (e.g., marketing, transactional) from the same domain, it is advisable to use separate keys for organizational convenience, although it is not mandatory. To generate these separate keys, you will need to employ different selectors. You have the flexibility to choose any name for your selector, allowing you to manage and differentiate the keys effectively.
 Empowering you with knowledge Empowering you with knowledge
Empowering you with knowledge Empowering you with knowledge